API and Bot Attacks Costing Businesses Billions and Rising
Security
Zaker Adham
20 September 2024
07 August 2024
|
Zaker Adham
Summary
Summary
Researchers from Pennsylvania State University have discovered multiple security vulnerabilities in 5G basebands, the processors that connect cellphones to mobile networks. These flaws could potentially allow hackers to covertly access and monitor users' devices.
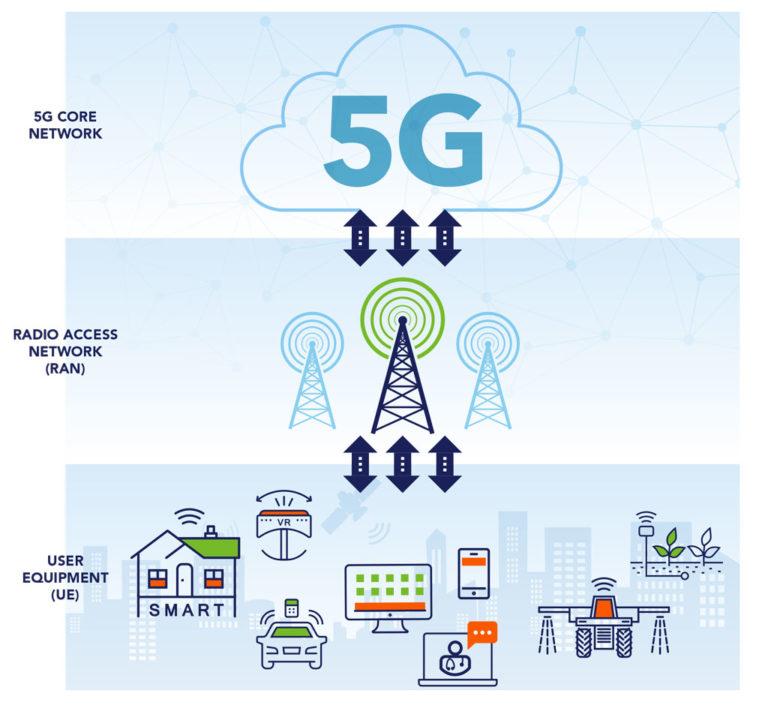
The findings were presented at the Black Hat cybersecurity conference in Las Vegas and detailed in an academic paper. Using a custom analysis tool named 5GBaseChecker, the team identified vulnerabilities in basebands produced by Samsung, MediaTek, and Qualcomm, which are found in devices from Google, OPPO, OnePlus, Motorola, and Samsung.
The research team, including Kai Tu, Yilu Dong, Abdullah Al Ishtiaq, Syed Md Mukit Rashid, Weixuan Wang, Tianwei Wu, and Syed Rafiul Hussain, has made 5GBaseChecker available on GitHub for other researchers to use in identifying 5G vulnerabilities.
Syed Rafiul Hussain, an assistant professor at Penn State, explained that they were able to deceive phones with vulnerable 5G basebands into connecting to a fake base station, essentially a counterfeit cellphone tower, to execute their attacks. Kai Tu, one of the students involved, noted that their most critical attack allowed them to fully exploit the phone from the fake base station, effectively compromising the security of 5G.
Tu further explained that by exploiting these vulnerabilities, a hacker could impersonate a victim's friend and send a phishing message or direct the victim to a malicious website to steal credentials. The researchers also demonstrated the ability to downgrade a victim's connection from 5G to older protocols like 4G, making it easier to eavesdrop on communications.
Most vendors have addressed and patched the identified vulnerabilities. Samsung confirmed it had released software patches, and Google also confirmed it had fixed the bugs. MediaTek and Qualcomm did not respond to requests for comment.

Security
Zaker Adham
20 September 2024

Security
Paikan Begzad
13 September 2024

Security
Zaker Adham
12 September 2024
Security
Paikan Begzad
26 August 2024